Tech Tip: Secure Cookies - What are they, when to use and how to set in 4D
PRODUCT: 4D | VERSION: 14.x | PLATFORM: Mac & Win
Published On: May 5, 2016
Much is talked about security on the web today and if all an application's web traffic is done using HTTPS, which is HTTP over SSL/TLS, to protect the data of the application layer, then this Tech Tip is not important. However, if any of the applicaiton"s web traffic is done using only HTTP, non secure web traffic, then this Tech Tip is important to the security of the site.
Securing cookies is an important. Think about an authentication cookie. When an attacker is able to grab this cookie, he or she can impersonate the user. This Tech Tip describes HttpOnly, secure flags that can enhance security of cookies adn how to set this flag from within 4D.
Let’s use the example of the authentication cookie and assume that XSS (cross-site scripting) vulnerability is present in the application. Then the attacker can take advantage of the XSS vulnerability to steal the authentication cookie. Can we somehow prevent this from happening? It turns out that an HttpOnly flag can be used to solve this problem. When an HttpOnly flag is used, JavaScript will not be able to read this authentication cookie.
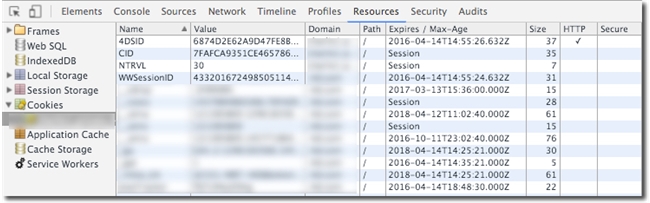
Note the 4DSID cookie that the HttpOnly flag is set automatically always. See the image below and note the HTTP column. Though the fact it can be seen in the browser that the flag is set, modern browsers block JavaScript from being able to access the cookie and prevents the cookie value from being used in an XSS attack.
For a more indepth decussion on the importance of securing cookies please read "Securing Cookies with HttpOnly and secure Flags."
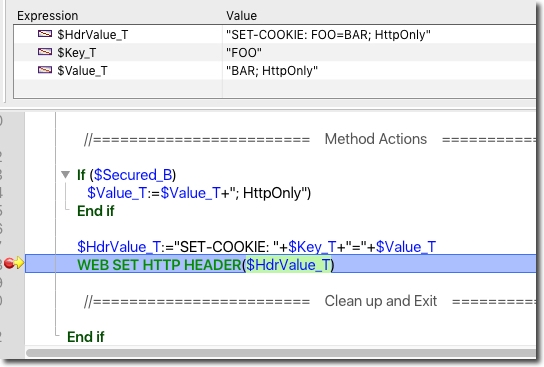
The utility shown below, Util_Web_SetCookie, demonstrates how to set the HttpOnly flag to an applicaiton cookie.
To set a secure cookie, call the utillity method as shown below.
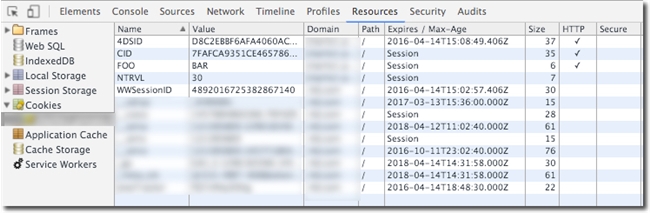
The image blow show the addition of the HttpOnly flag being set to application cookies.
The image below shows the HttpOnly flags set in the web browser.
Securing cookies is an important. Think about an authentication cookie. When an attacker is able to grab this cookie, he or she can impersonate the user. This Tech Tip describes HttpOnly, secure flags that can enhance security of cookies adn how to set this flag from within 4D.
Let’s use the example of the authentication cookie and assume that XSS (cross-site scripting) vulnerability is present in the application. Then the attacker can take advantage of the XSS vulnerability to steal the authentication cookie. Can we somehow prevent this from happening? It turns out that an HttpOnly flag can be used to solve this problem. When an HttpOnly flag is used, JavaScript will not be able to read this authentication cookie.
Note the 4DSID cookie that the HttpOnly flag is set automatically always. See the image below and note the HTTP column. Though the fact it can be seen in the browser that the flag is set, modern browsers block JavaScript from being able to access the cookie and prevents the cookie value from being used in an XSS attack.
For a more indepth decussion on the importance of securing cookies please read "Securing Cookies with HttpOnly and secure Flags."

The utility shown below, Util_Web_SetCookie, demonstrates how to set the HttpOnly flag to an applicaiton cookie.
| If (True) If (False) Begin SQL /* Name: Util_Web_SetCookie Path: Util_Web_SetCookie Purpose: Set a cookie to the HTTP header $1 - TEXT - The key to the cookie $2 - TEXT - The value to the cookie $3 - BOOL - True for a secure cookie, false if not */ End SQL End if C_TEXT($MethodName_T) $MethodName_T:=Current method name //===================== Declare Variables ================================== //method_parameters_declarations C_TEXT($Key_T;$1) C_TEXT($Value_T;$2) C_BOOLEAN($Secured_B;$3) //-------------------------------------------------------------------------- //method_wide_constants_declarations //-------------------------------------------------------------------------- //local_variable_declarations C_LONGINT($Ndx;$SOA;$RIS;$Params_L) C_TEXT($HdrValue_T) End if //====================== Initialize and Setup ================================ $Params_L:=Count parameters If ($Params_L>=2) $Key_T:=$1 $Value_T:=$2 If ($Params_L>2) $Secured_B:=$3 End if //======================== Method Actions ================================== If ($Secured_B) $Value_T:=$Value_T+"; HttpOnly") End if $HdrValue_T:="SET-COOKIE: "+$Key_T+"="+$Value_T WEB SET HTTP HEADER($HdrValue_T) //======================== Clean up and Exit ================================= End if |
To set a secure cookie, call the utillity method as shown below.
| Util_Web_SetCookie ("FOO";"BAR";True) |
The image blow show the addition of the HttpOnly flag being set to application cookies.

The image below shows the HttpOnly flags set in the web browser.

