Tech Tip: Prevent Injection Attacks in ORDA Queries by Using Placeholders
PRODUCT: 4D | VERSION: 19 | PLATFORM: Mac & Win
Published On: October 31, 2022
Injection attacks cover a set of ways for attackers to insert, or inject, malicious code into a program. There are various types out there that can drastically affect the infrastructures and security of applications and databases—and 4D is no exception. Within 4D, injection attacks can occur at the web frontend, where user inputs sent over the web are put into 4D database queries. With ORDA queries specifically, there is a vulnerable way and a best practice to structure your queries when it comes to preventing injection attacks.
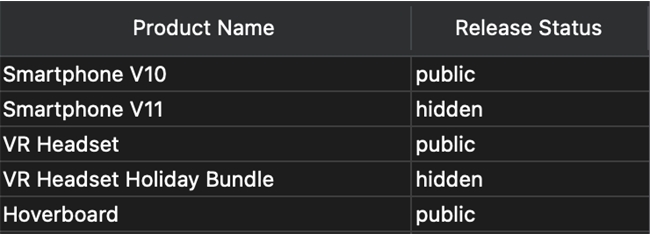
Here is an example of a table where an e-commerce business stores its public and unreleased products:
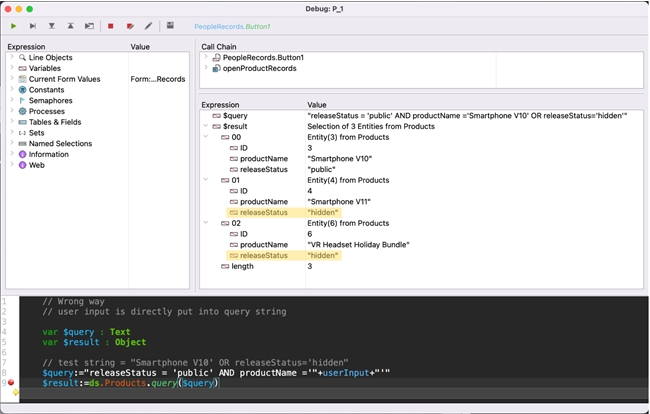
Vulnerable way:
One way to construct an ORDA query is to insert user inputs into a string via variables and saving this string into a variable; however, this can leave the query vulnerable to injection attacks as the user can easily add parts to the query and output unintended results.
In the following piece of code, the developer intends the user to only input a product name, but if inputted, “Smartphone V10' OR releaseStatus='hidden” can allow attackers to view unreleased products.
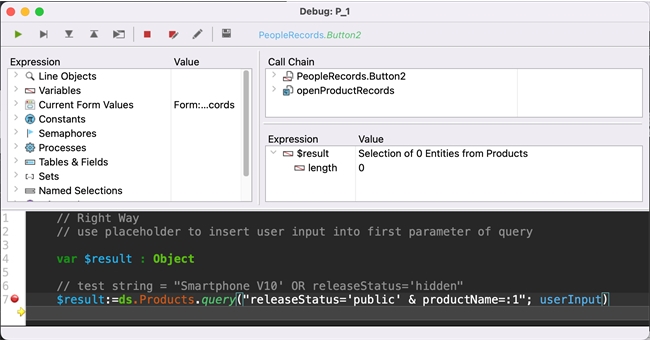
Best practice:
The better way to construct an ORDA query is to use placeholders, which parametrize the query into a set of conditions (i.e., split the query into parts). By using placeholders, attackers cannot rewrite the whole query.
In this improved line of code, the attacker’s input “Smartphone V10' OR releaseStatus='hidden” would cause the query to fail, since there is no product of this name.
Here is an example of a table where an e-commerce business stores its public and unreleased products:

Vulnerable way:
One way to construct an ORDA query is to insert user inputs into a string via variables and saving this string into a variable; however, this can leave the query vulnerable to injection attacks as the user can easily add parts to the query and output unintended results.
In the following piece of code, the developer intends the user to only input a product name, but if inputted, “Smartphone V10' OR releaseStatus='hidden” can allow attackers to view unreleased products.
| $query:="releaseStatus = 'public' AND productName ='"+userInput+"'" $result:=ds.Products.query($query) |

Best practice:
The better way to construct an ORDA query is to use placeholders, which parametrize the query into a set of conditions (i.e., split the query into parts). By using placeholders, attackers cannot rewrite the whole query.
In this improved line of code, the attacker’s input “Smartphone V10' OR releaseStatus='hidden” would cause the query to fail, since there is no product of this name.
| $result:=ds.Products.query("releaseStatus='public' & productName=:1"; userInput) |

